IPv4 IPSec doesn’t support multicast, we need to use GRE (unicast) to
encapsulate multicast traffic and encrypt it. As a consequence, more
complication and an additional level of routing, so less performance.
One of the advantages of IPv6 is the support of IPSec authentication
and encryption (AH, ESP) right in the extension headers, which makes it
natively support IPv6 multicast.
In this lab we will be using IPv6 IPSec site-to-site protection using VTI to natively support IPv6 multicast.
The configuration involves three topics: IPv6 routing, IPv6 IPSec and
IPv6 multicast. Each process is built on the top the previous one, so
before touching IPsec, make sure you have local connectivity for each
segment of the network and complete reachability through IPv6 routing.
Next step, you can move to IPv6 IPSec and change routing configuration accordingly (through VTI).
IPv6 multicast relies on a solid foundation of unicast reachability,
so once you have routes exchanged between the two sides through the
secure connection you can start configuring IPv6 multicast (BSR, RP,
client and server simulation).
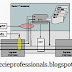
Picture1: Lab topology

Lab outline
- Routing
- OSPFv3
- EIGRP for IPv6
- IPv6 IPSec
- Using IPv6 IPSec VTI
- Using OSPFv3 IPSec security feature
- IPv6 Multicast
- IPv6 PIM BSR
- Offline lab
- Troubleshooting cases
- Performance testing
Routing
| Note: IPv6 Routing relies on link-local addresses, so for troubleshooting purpose, link-local IPs are configured to be similar to their respective global addresses, so they are easily recognisable. This will be of a tremendous help during troubleshooting. Otherwise you will find yourself trying to decode the matrix : )  |
Needs an interface configured with IPv4 address for Router-id
OSPFv3 offloads security to IPv6 native IPv6, so you can secure OSPFv3 communications on purpose: per- interface or per-area basis.








0 comments:
Post a Comment