DHCPv6 relies on stateless UDP communication using UDP 546 and UDP 547 ports. As stated in the RFC 3315 this makes DHCPv6 particularly vulnerable to fake attack, in which SOLICIT messages are generated with random source prefixes.
Using DHCPv6 Rapid-Commit mode, ONLY two messages are exchanged between the client and the server to get an IPv6 prefix.
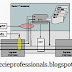
Picture1: lab topology – IOS 12.4(24)T implemented in GNS3

DHCPv6 server configuration:
| ipv6 dhcp pool SLAAC-POOL address prefix 2001:DB8:5AB::/64 lifetime infinite infinite dns-server 2001:DB8:5AB::57 domain-name nouri.com ! interface FastEthernet1/0 ip address 192.168.0.202 255.255.255.0 ipv6 address 2001:DB8::202/64 ipv6 enable ipv6 dhcp server pool0 rapid-commit end |
| interface FastEthernet1/0 switchport access vlan 10 ! interface FastEthernet1/1 switchport mode trunk |
You can enter manually the DHCPv6 sever MAC address from the local neighbor table of through a script by pinging all DHCP agents multicast address FF02::1:2.
SOLCIT messages are sent blindly without even expecting any responses.








0 comments:
Post a Comment