This post is dedicated to the best practise for setting up CCIE R&S lab and I want to show you how to set up a practise rack to where you will never ever have to switch a single cable again , no matter what your lab topology looks like , the set up that does it all !
The only difference between this one and the previous topology is that I have changed the symbols so it’s easier to differentiate devices on screen but except for that it is all the same and no other changes have been made. Further down I have added initial configs files for CBT Nuggets CCIE series, INE , IP Expert and Narbik (Super Lab)
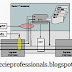
CCIE R&S topology I have built and been using on GNS3 for the CCIE journey.
So far I have seen and used topologies with a GNS3 built in Frame Relay switch plus 6 routers (INE spec) so I’ve decided to create one with CLI configurable Frame Switch and connect all devices in a way so that you are able to create any topology without the need of changing the cabling etc … The reason for 17 devices being used is because some of the CCIE preparation series like IP Expert, CCIE Service Provider see image have topologies with more than 6 routers which is expectable from Cisco in the current v4 Lab exam but the idea is so we can practise not only INE lab scenarios with 6 routers but also IP Expert lab scenarios where Quadruple CCIE Scott Morris uses topology with 9 routers instead and of course for us to become more familiar with the actual frame relay switch configuration.
In case you having some issues with connectivity or the gns3 is crashing just after you start the topology, change the (127.0.0.1 with localhost) or vice versa in the .net file.
Please remember, that you can’t run most of layer 2 technologies command, since GNS3 (and all emulators) just do the software, where switches are mostly ASIC programmed to run the features.
This topology is customizable which means that with a little tweaking (vlans, ip addreses, frame switch config etc…) you will be able to practise any R&S scenario you can possibly find out there.
See intial configs below – INE lab specification VOL1
Frame_switch BB1 BB2 BB3 R1 R2 R3 R4 R5 R6 SW1 SW2 SW3 SW4

See intial configs below – IP Expert lab specification VOL1
FRAME_SWITCH BB1 BB2 BB3 SW1 SW2 SW3 SW4 R1 R2 R4 R5 R6 R7 R8 R9

See intial configs below – CBT Nuggets lab specification (CCIE R&S LAB SERIES)
CBT_BB1 FRAME_SWITCH_CBT CBT_SW1 CBT_SW2 CBT_SW3 CBT_SW4
CBT_R1 CBT_R2 CBT_R3 CBT_R4 CBT_R5 CBT_R6 CBT_R7

See intial configs below – Narbik Super Lab specification (CCIE R&S LAB SERIES)
SW1 – SW2 – SW3 – SW4
vlan data
vlan 111
vlan 112
vlan 113
vlan 3
apply
exit